Table of contents
- Introduction to Computer Network
- Types of Computer Network
- Important Network Terminologies
- Use case of Computer Networks
- The internet and computer networks
- How do they work?
- Architecture
- Network Topology
- Types of Network Topology
- Computer Network Security
- Mesh networks
- Types of mesh networks
- Load balancers and networks
- Content delivery networks
Learn how computer networks work, the architecture used to design networks, and how to keep them secure in this introduction to networking.
Introduction to Computer Network
A computer network consists of two or more computers that are connected by cables or wireless, with the purpose of sharing data and resources.
A computer network is defined by geographic location. A local area network (LAN) connects computers in a defined physical space like an office building, whereas a wide area network (WAN) can connect computers across continents.
Every business, entertainment, and research uses computer networks.
Types of Computer Network
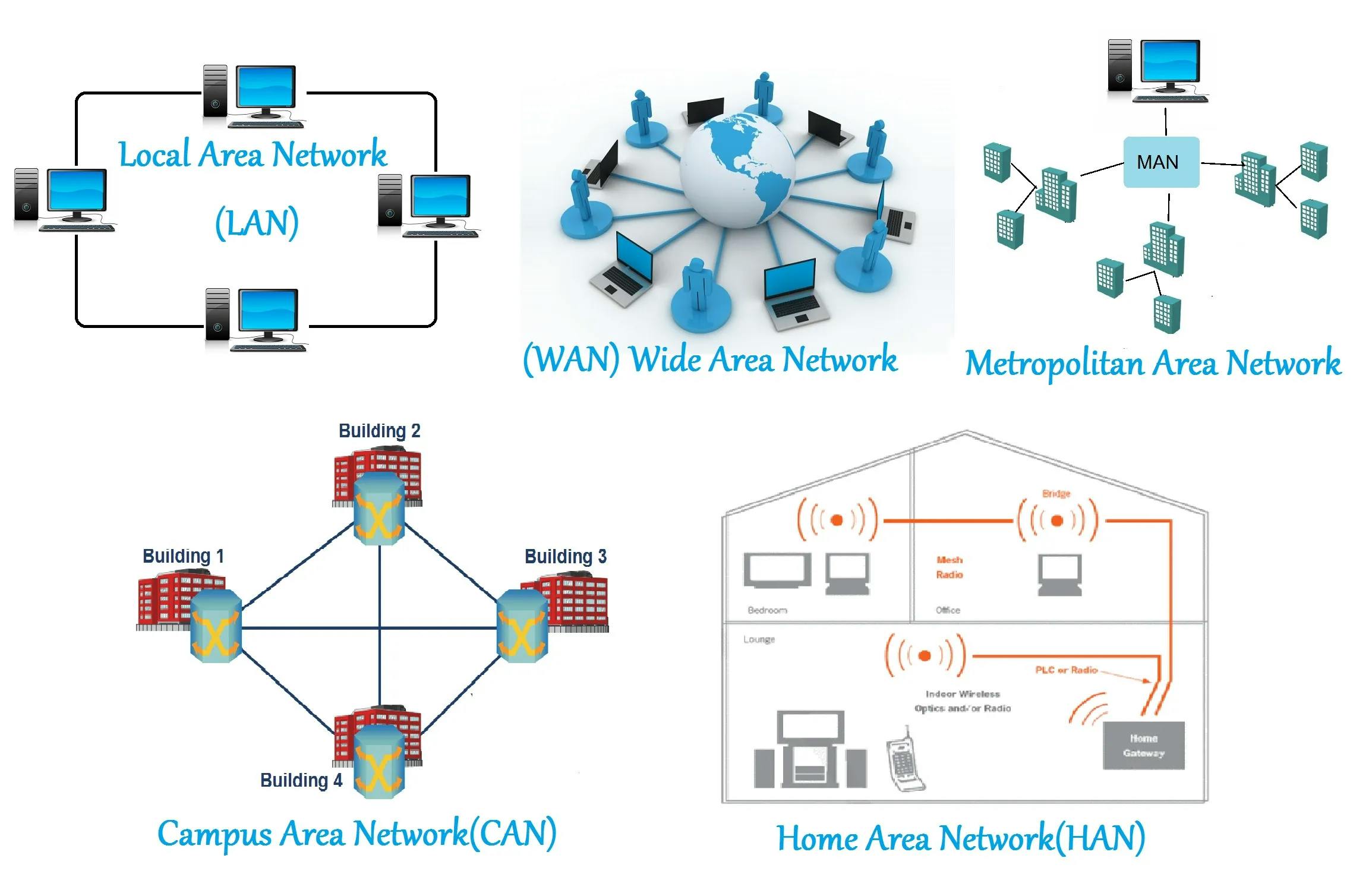
Local Area Network
A local area network is a network that connects computers over a short distance. A computer network may connect all the computers in a building.
Wireless Local Area Network
A wireless local area network is just like a local area network, but connections between devices on the network are made without wires.
Wide Area Network
A wide area network is a network that connects computers over a wide area. Billions of computers are connected to the internet.
Metropolitan Area Network
Metropolitan Area Network are larger than Local Area Network but smaller than Wide Area Network. They are typically owned and managed by cities and government entities.
Personal Area Network
Personal Area Network serves one person. If you have an Apple device and a Mac, it is very likely that you have set up a PAN that shares and syncs content.
Storage Area Network
A SAN is a specialized network that provides access to block-level storage that, to the user, looks and works like a storage drive that is physically attached to a computer.
Campus Area Network
A CAN is a corporate area network. A CAN is smaller than a WAN. Colleges, universities, and business campuses are served by CANs.
Virtual Private Network
A virtual private network is a secure, point-to-point connection between two network end points. The identity and access credentials of a user are kept safe when using a virtual private network.
Important Network Terminologies

IP Address
Every device connected to a network that uses the Internet Protocol for communication has a unique number assigned to it. The host network and the location of the device on the host network are identified by each IP address. When one device sends data to another, the data includes the sender's and destination's addresses.
Node
A connection point is inside a network that can receive, send, create, or store data. You have to give a form of identification to receive access. Computers, printers, modems, bridges, and switches are some of the examples of nodes. Any network device that can recognize, process, and transmit information to any other network device is a node.
Routers
A routers is a device that sends information between networks. The best way to get the information to its final destination is determined by the routers. Data packets are forwarded until they reach their destination.
Switch
A switch is a device that connects other devices and manages communication within a network. A switch sends information between networks when it is in a single network. Data is transferred between devices in a computer network. There are three types of switches.
Circuit Switch
A circuit switch establishes a dedicated communication path. No other traffic can travel along that path because the full bandwidth is available during the transmission.
Packet Switch
Because of their small size, packets make less demands on the network. The packets travel through the network.
Message Switch
Sending a message in its entirety from source to destination is what message switch does.
Port
A port is a connection between network devices. The suites or room numbers within a hotel are referred to as ports, if you think of an internet address as similar to the address of a hotel. Port numbers are used to determine which application, service, or process should receive certain messages.
Network Cable Types
The most common network cable types are twisted pair, coaxial, and fiber optic. The size of the network, the arrangement of network elements, and the physical distance between devices are some of the factors that affect the choice of cable type.
Use case of Computer Networks
A computer network is a combination of the wired and wireless connection of two or more computers. Almost every digital device is connected to a computer network.
In an office setting, you and your colleagues may have access to a printer or a group messaging system. The computing network that allows this is likely a local area network.
A city government might be able to manage a network of cameras. This network would allow city emergency personnel to respond to traffic accidents, advise drivers of alternate travel routes, and even issue traffic tickets to drivers who run red lights.
The Weather Company created a peer-to-peer mesh network that allows mobile devices to communicate directly with other mobile devices. Billions of people can receive life-saving weather information, even without an internet connection, thanks to the Mesh Network Alerts project.
The internet and computer networks

Billions of digital devices are connected to the internet. Communication between these devices is allowed by standard protocols. The hypertext transfer protocol is in front of all website addresses. Every device that uses the internet requires a unique identifying number. Unique location information is provided by your mailing address so that information can be delivered correctly.
The infrastructure that allows the transmission of packets of data or information over the internet is provided by Internet Service Providers and Network Service Providers. Every piece of information sent over the internet goes to different devices. The combination of protocols and infrastructure tells where to go.
How do they work?
Devices in a network can communicate and share resources. Protocols define how communications are sent and received. The protocols allow devices to communicate. Each device on a network uses an Internet Protocol address, a string of numbers that uniquely identifies it and allows other devices to recognize it.
Virtual or physical devices are used to facilitate communications. The best way for data to reach its ultimate destination is determined by the routers. Network switches connect devices and manage communication inside the network to ensure that information travels to its final destination.
Architecture
The physical and logical framework of a computer network is defined by computer network architecture. It shows how the network organizes computers and what tasks are assigned to them. Hardware, software, transmission media, network topology, and communications protocols are components of the network architecture.
Types of network architecture
P2P and client/server are two types of network architecture.
P2P Network Architecture
In P2P architecture, two or more computers are connected as peers, meaning they have the same power and privileges on the network. A P2P network doesn't need a central server for coordination. Each computer on the network is a client and a server, and they both serve the needs of the client. Sharing storage, memory, bandwidth, and processing power is what each peer makes available to the network.
Client/server Network Architecture
In a client/server network, a central server manages resources and delivers services to client devices in the network. The clients in the network communicate with each other. Unlike the P2P model, clients in a client/server architecture don't share resources. A tiered model is an architecture type that is designed with multiple levels.
Network Topology
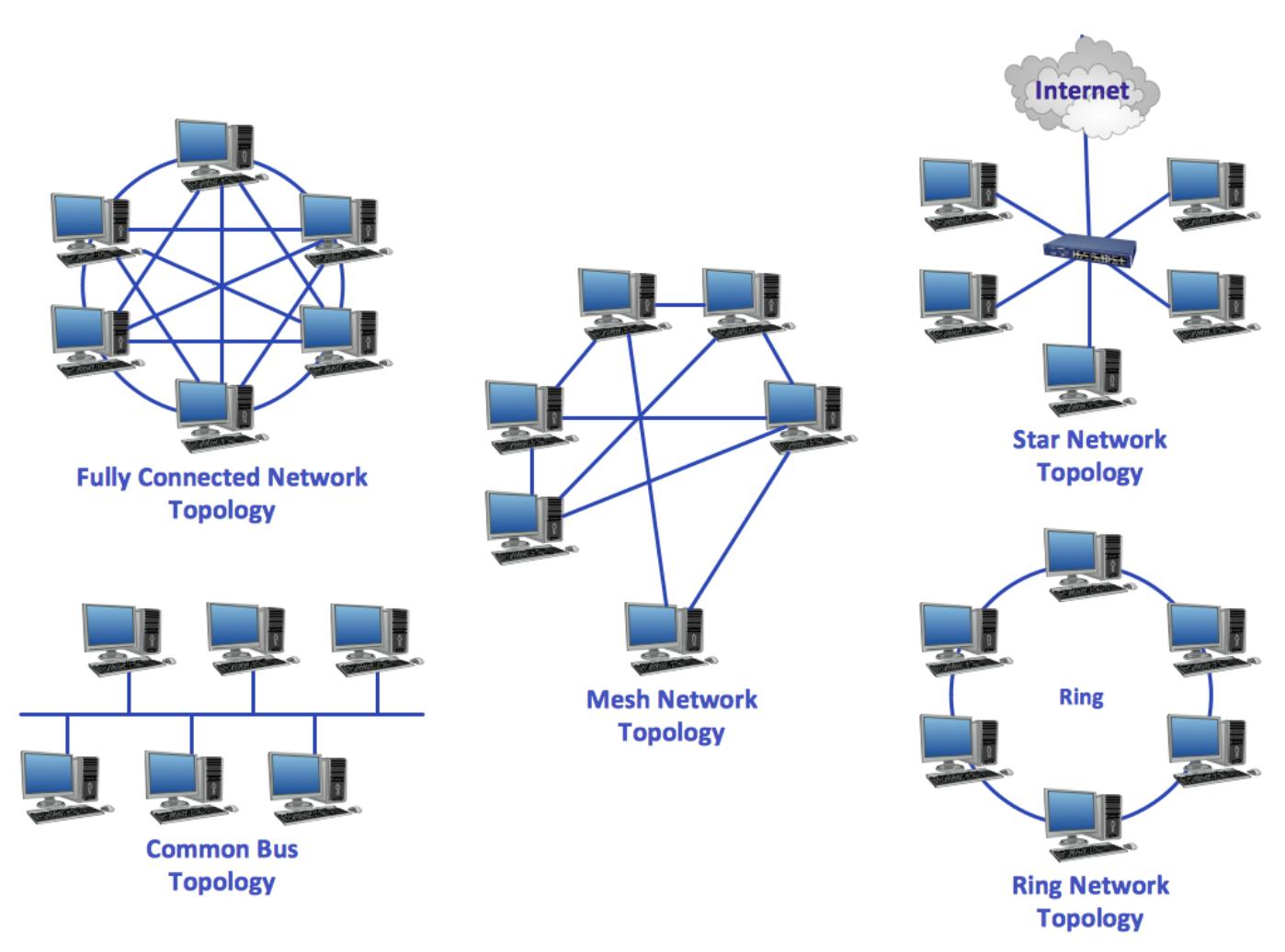
A network is a device that can send, receive, and store data. A network link can be cabled or wireless. Bus, ring, star, and mesh are the most common topologies.
Types of Network Topology
Bus Network Topology
A bus network topology is when every network is connected to a main cable.
Ring Network Topology
Each device has two neighbors in a ring topology. Adjacent pairs are connected directly, while non-adjacent pairs are connected indirectly.
Star Network Topology
In a star network, all the nodes are connected to a single hub and each is connected through that hub.
Mesh Network Topology
A mesh is defined by connections. There is a way to create a full mesh network. You can create a partial mesh topology in which only some of the nodes are connected to each other and the other is connected to the most data. It's often reserved for networks that require high redundancy because it's expensive and time-consuming to execute. It is more cost effective and simpler to execute partial mesh.
Computer Network Security
Computer network security protects the integrity of information contained in a network. The need to control access to information is balanced by the need to provide service to users.
The network has many entry points. The hardware and software that comprise the network as well as the devices used to access it are included in the entry points. Several defense methods are required because of the entry points. Defenses may include devices that monitor network traffic and prevent access to parts of the network based on security rules.
Security includes isolating network data so that it is harder to access than less critical information. Ensuring hardware and software updates and patches are performed regularly, educating network users about their role in security processes, and staying aware of external threats executed by hackers are some of the other network security measures.
Updating security procedures is required for the use of public cloud. A secure cloud requires a secure underlying network.
Mesh networks
A mesh network is a type of network in which the computer network's nodes connect to as many other computers as possible. The data can be efficiently routed to its destination. The fault tolerance is increased by the fact that there are many other nodes that can transmit data. The mesh networks self-organize and search for the most reliable path to send information.
Types of mesh networks
There are two types of mesh networks.
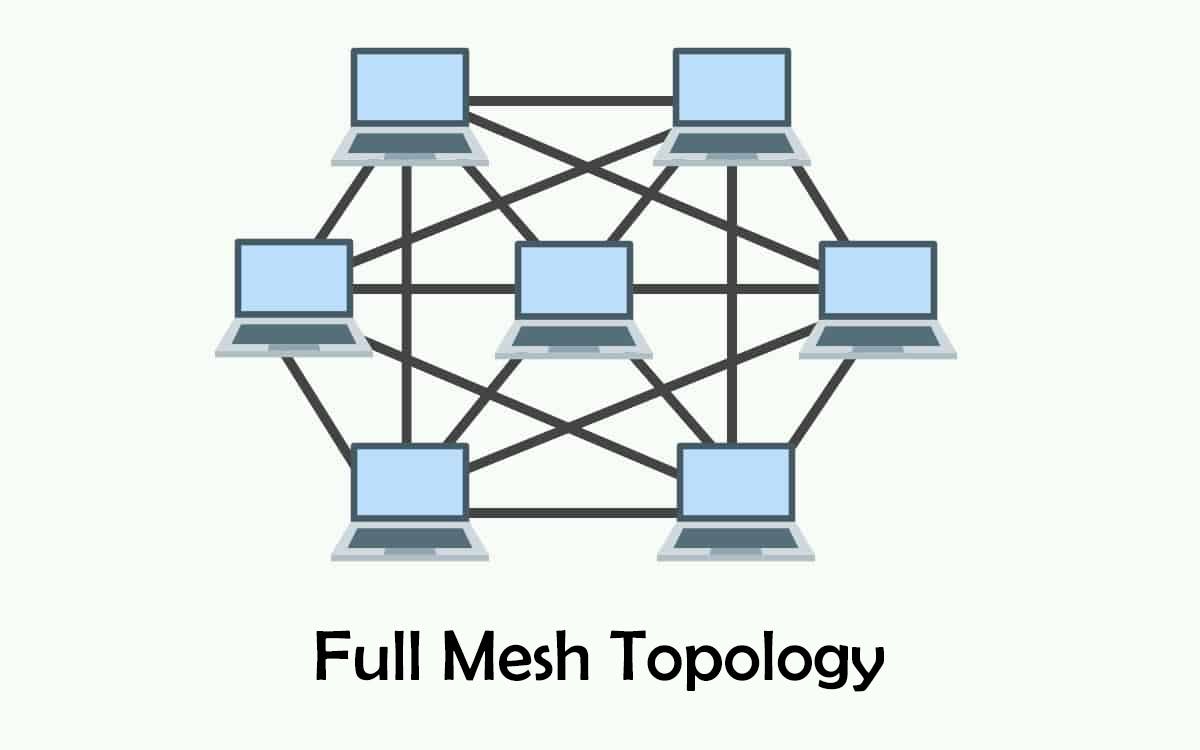
Full Mesh Topology
The highest level of fault tolerance can be found in a full mesh network. It costs more to execute. In a partial mesh topology, the most frequently connected are the ones that exchange the most data.
Wireless Mesh Topology
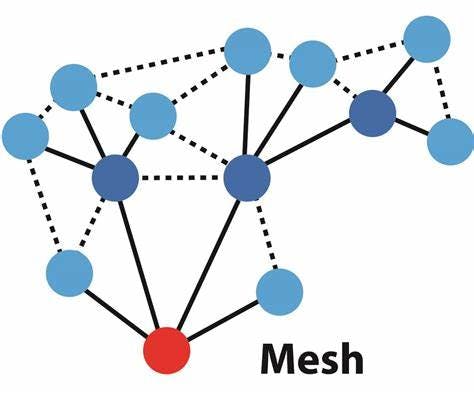
A wireless mesh network may have hundreds to tens of nodes. This type of network has access points spread across a large area.
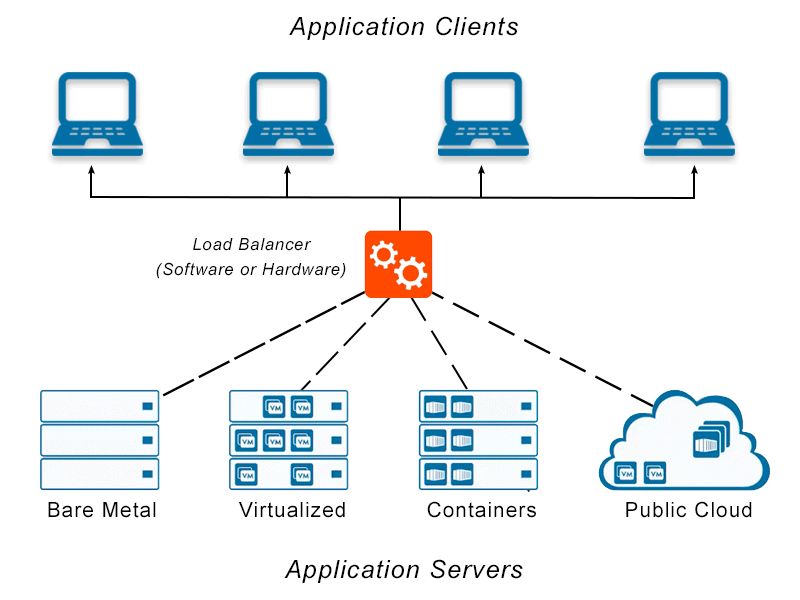
Load balancers and networks
Load balancers efficiently distribute workload and network traffic. The load balancer watches all traffic coming into a network and directs it to the best place to manage it. Load balancing aims to avoid resource overload, improve response times, and maximize throughput.
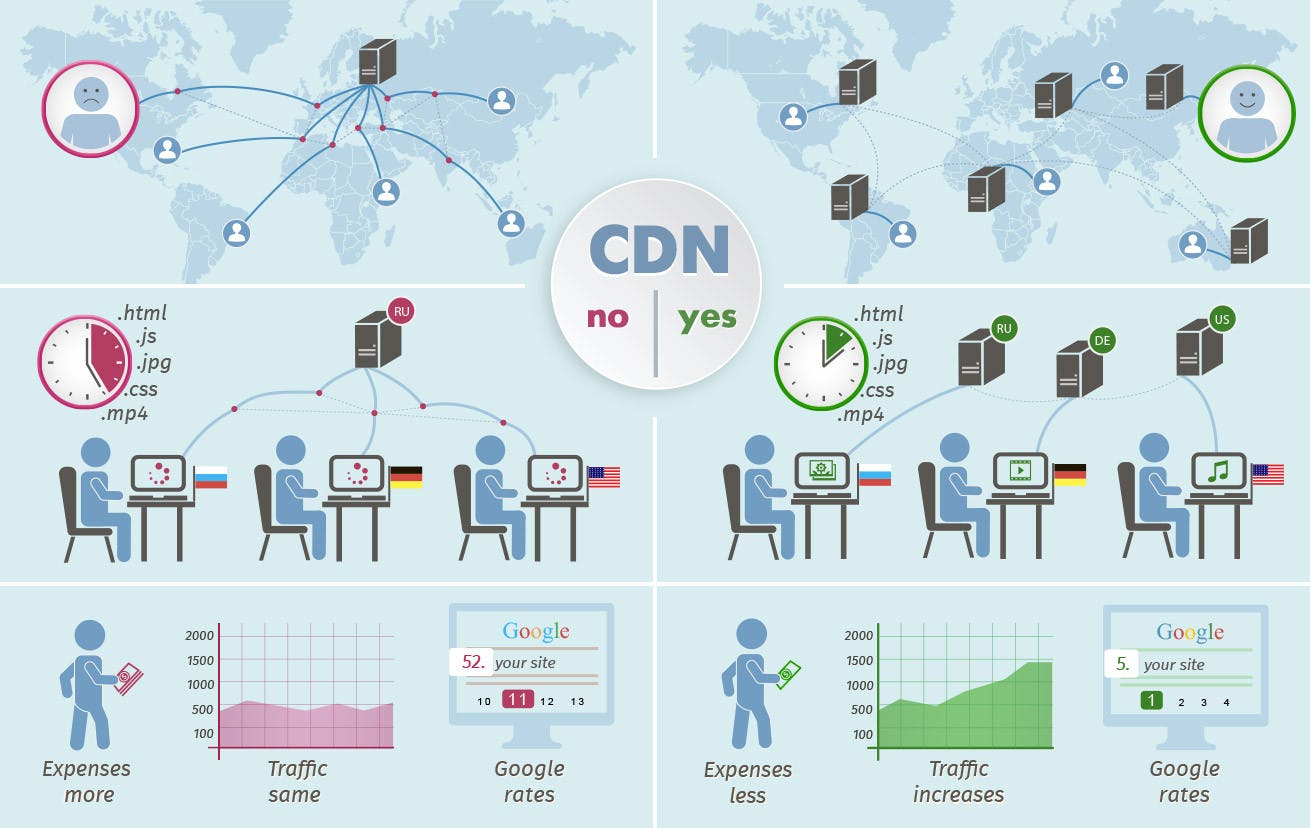
Content delivery networks
A content delivery network is a distributed server network that delivers temporarily stored, or cached, copies of website content to users based on their geographic location. The distance between your website visitors and your website server can be reduced with the help of a CDN. It's easier to serve content to your end users if you have it closer to them. The impact of hacks and attacks can be mitigated by introducing a layer between the end user and your website infrastructure.
Live-streaming media, on-demand media, gaming companies, application creators, e-commerce sites, are some of the companies that use content delivery networks to better serve consumers.
Gratitude for perusing my article till end. I hope you realized something unique today. If you enjoyed this article then please share to your buddies and if you have suggestions or thoughts to share with me then please write in the comment box.